Malicious PowerShell Targeting Cryptocurrency Browser Extensions
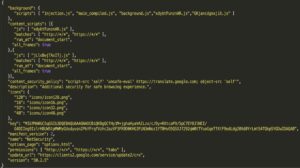
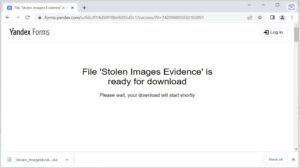
A PowerShell script was found targeting cryptocurrency browser extensions or apps, including Edge, Chrome, and Brave. The hackers could replace a wallet address with their own to steal funds. Ref https://isc.sans.edu/diary/Malicious+PowerShell+Targeting+Cryptocurrency+Browser+Extensions/28772