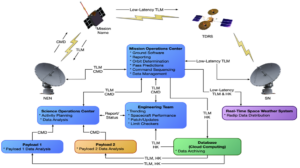
Frameworks for Addressing Satellite Cybersecurity
Two recently-released cybersecurity frameworks address cybersecurity issues faced by the ground control systems and the space-based infrastructure of the space sector. New guidance from the US National Institute of Standards…