Silverfort researchers revealed a bypass for Microsoft’s Active Directory Group Policy disabling NTLMv1, exploiting a misconfigured Netlogon Remote Protocol setting. Despite policy restrictions, applications can re-enable NTLMv1, risking relay attacks. More https://www.silverfort.com/blog/ntlmv1-bypass-in-active-directory-technical-deep-dive/
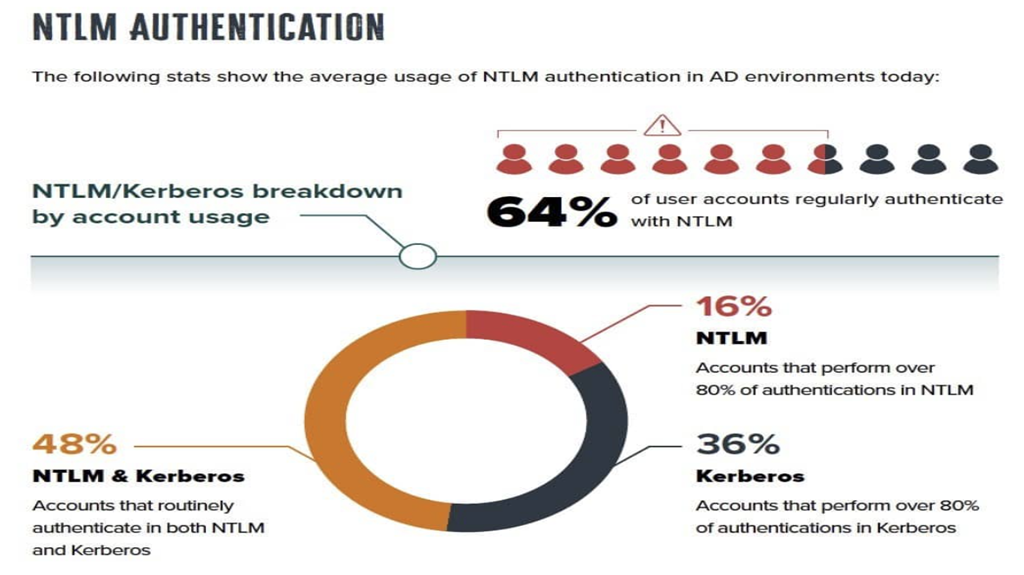
Understanding the Security Risks of NTLM
- Post author:System
- Post published:18 January 2025
- Post category:Blog & News